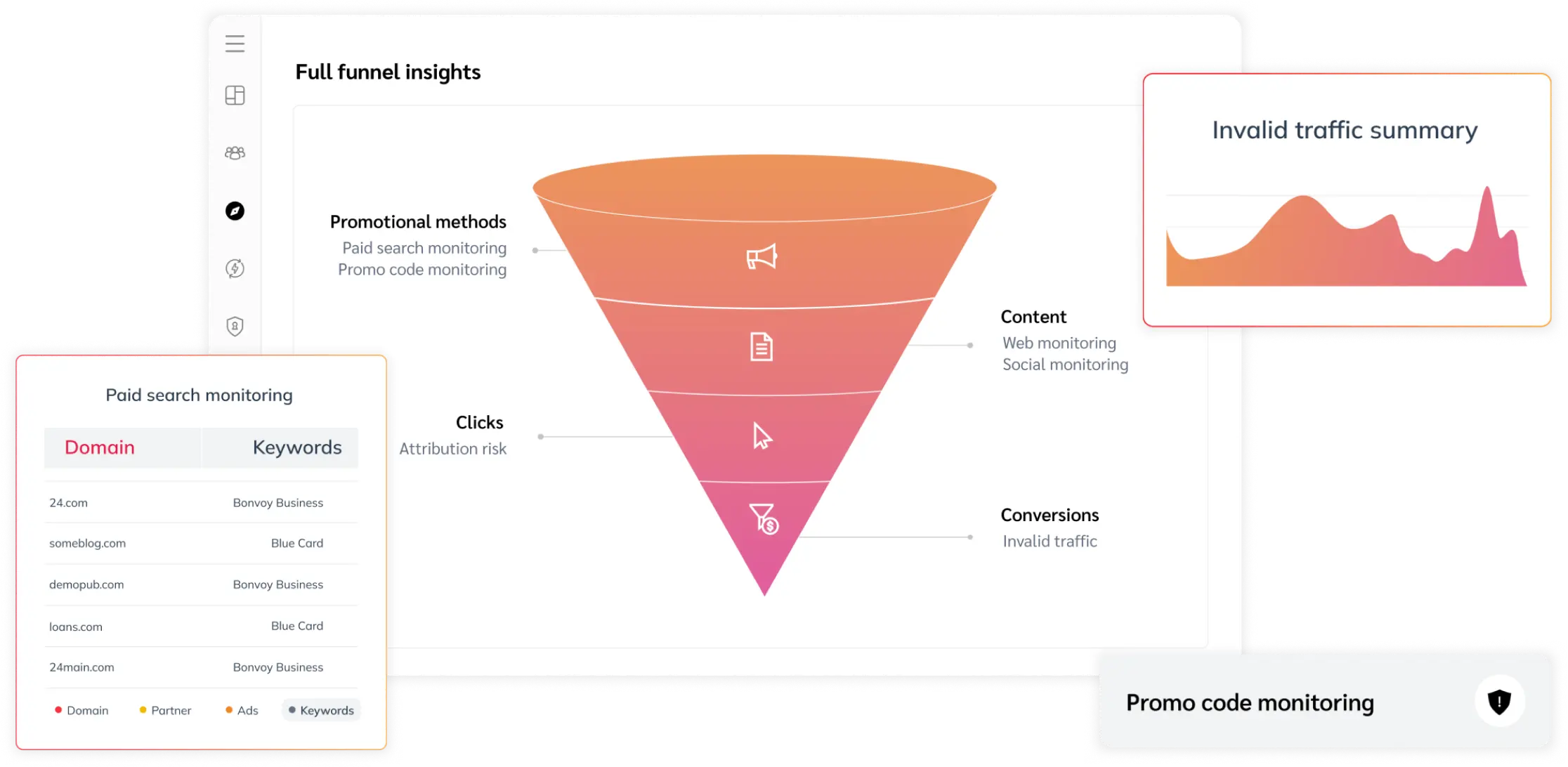
PROTECT & MONITOR
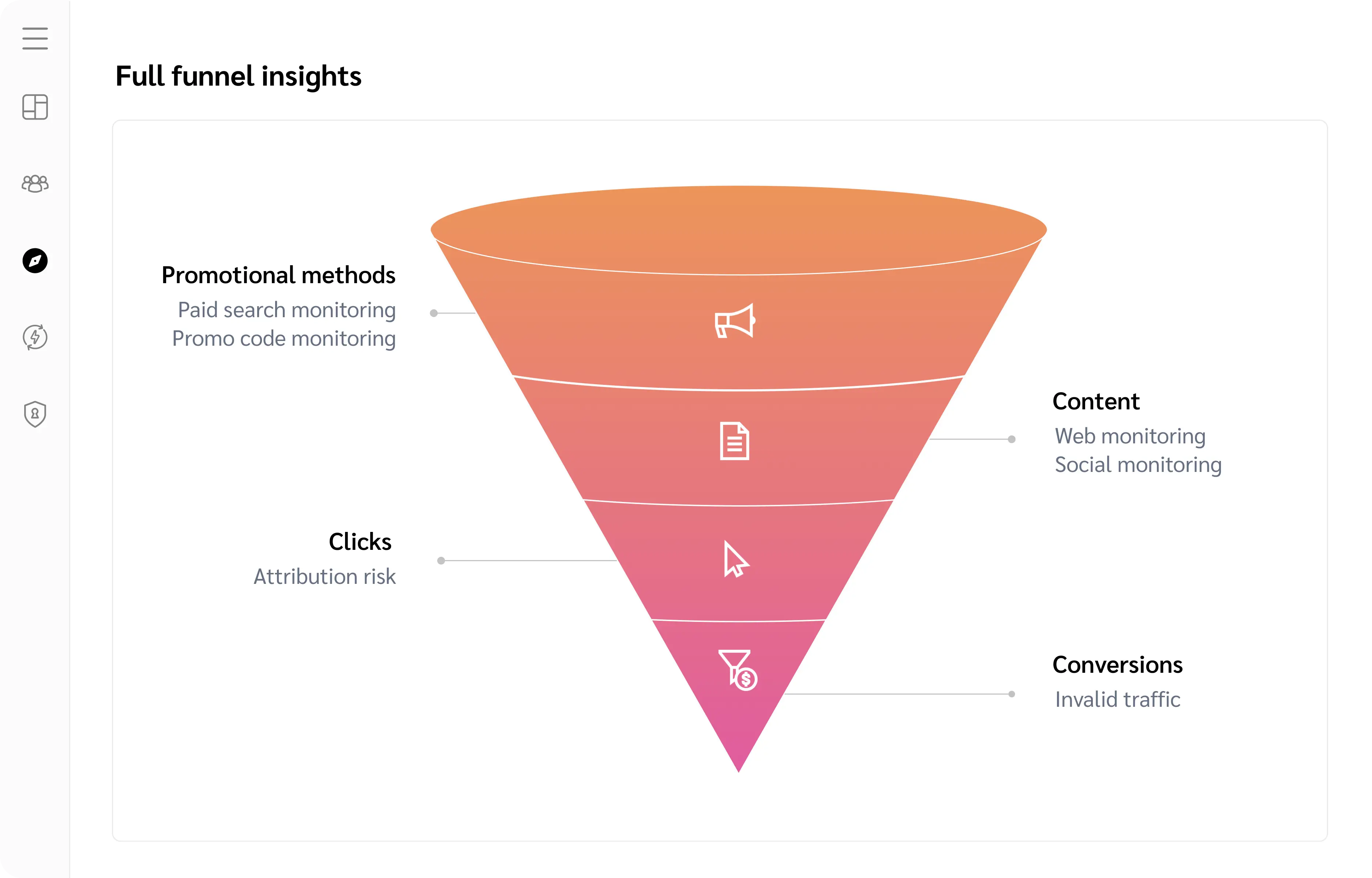
Full-funnel program protection
Safeguard your brand and fortify your partnerships.
No need for third-party tools
Get a truly integrated solution with protection in the same platform as partnership management.
Save time and resources
Automate your daily monitoring and streamline your remediation workflows.
Confidently scale your partnership program
Create a safe environment for more productive partnerships, larger programs, and increased revenue.
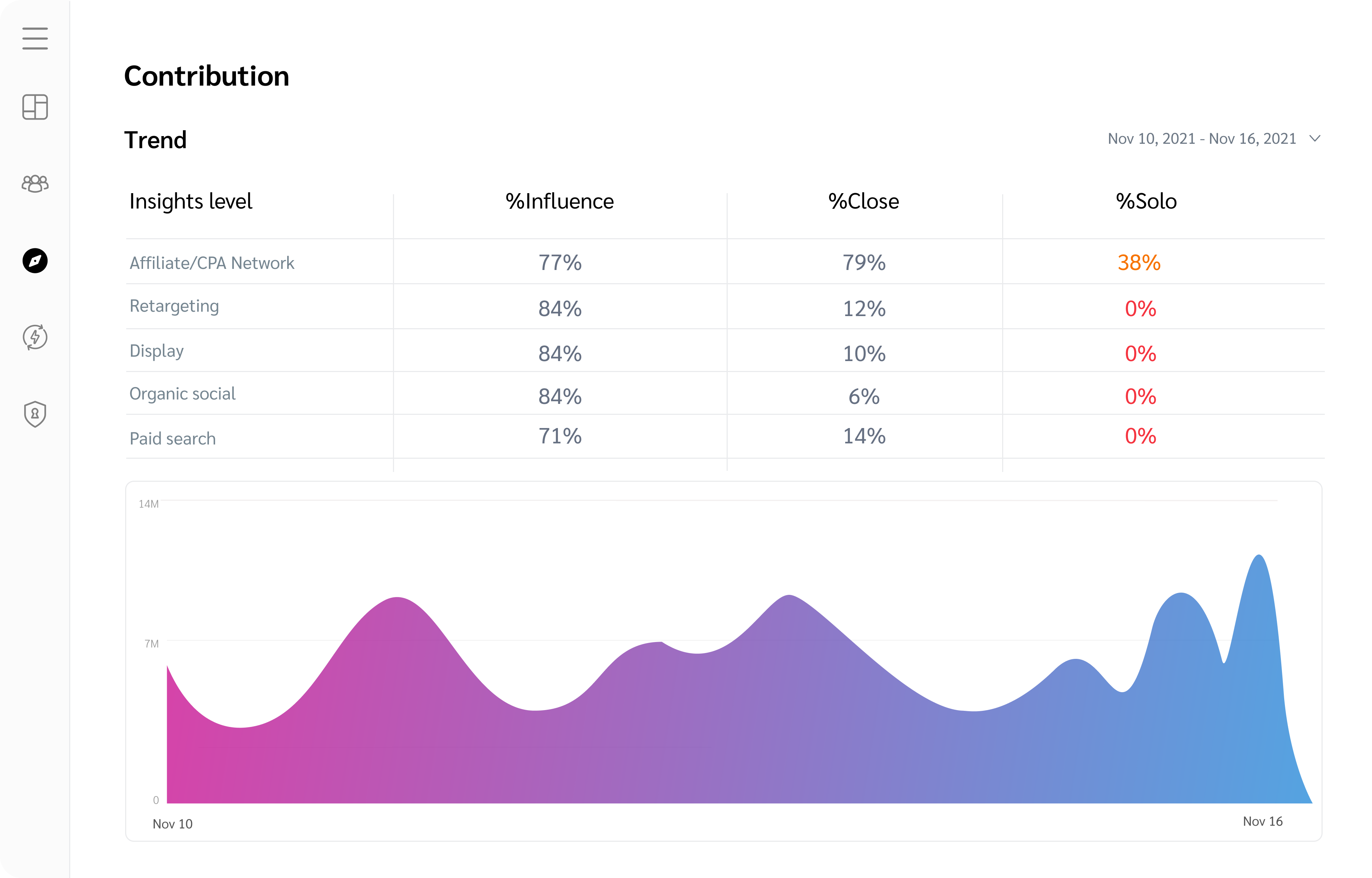
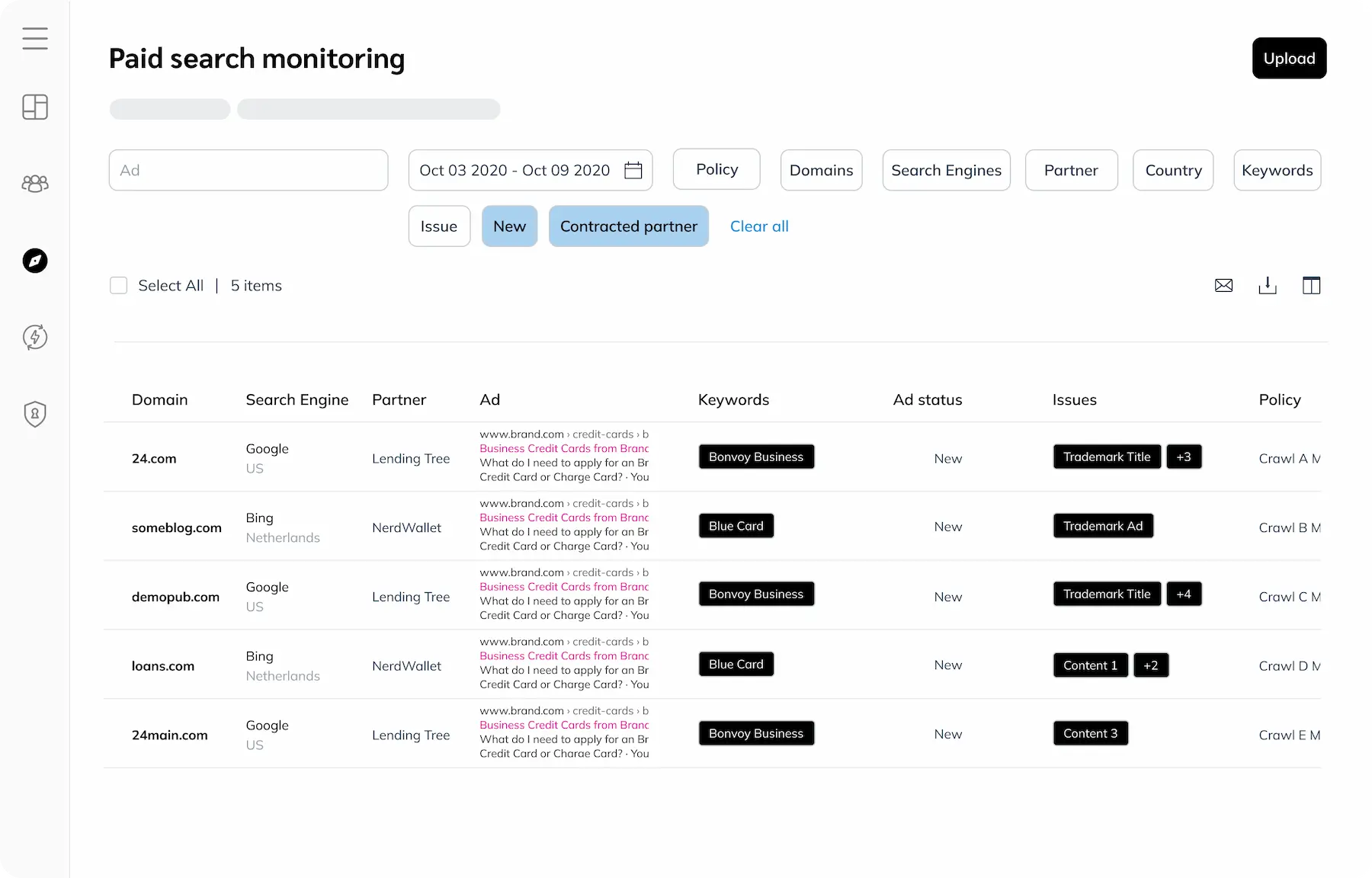
Find and resolve keyword violations quickly
Your branded keywords ensure your customers find you first when searching online. But you lose sales from high-intent customers when your keywords are used by other websites. Paid Search Monitoring equips you with all the tools necessary to protect your valuable assets, including keyword monitoring, enforcement, and resolution.
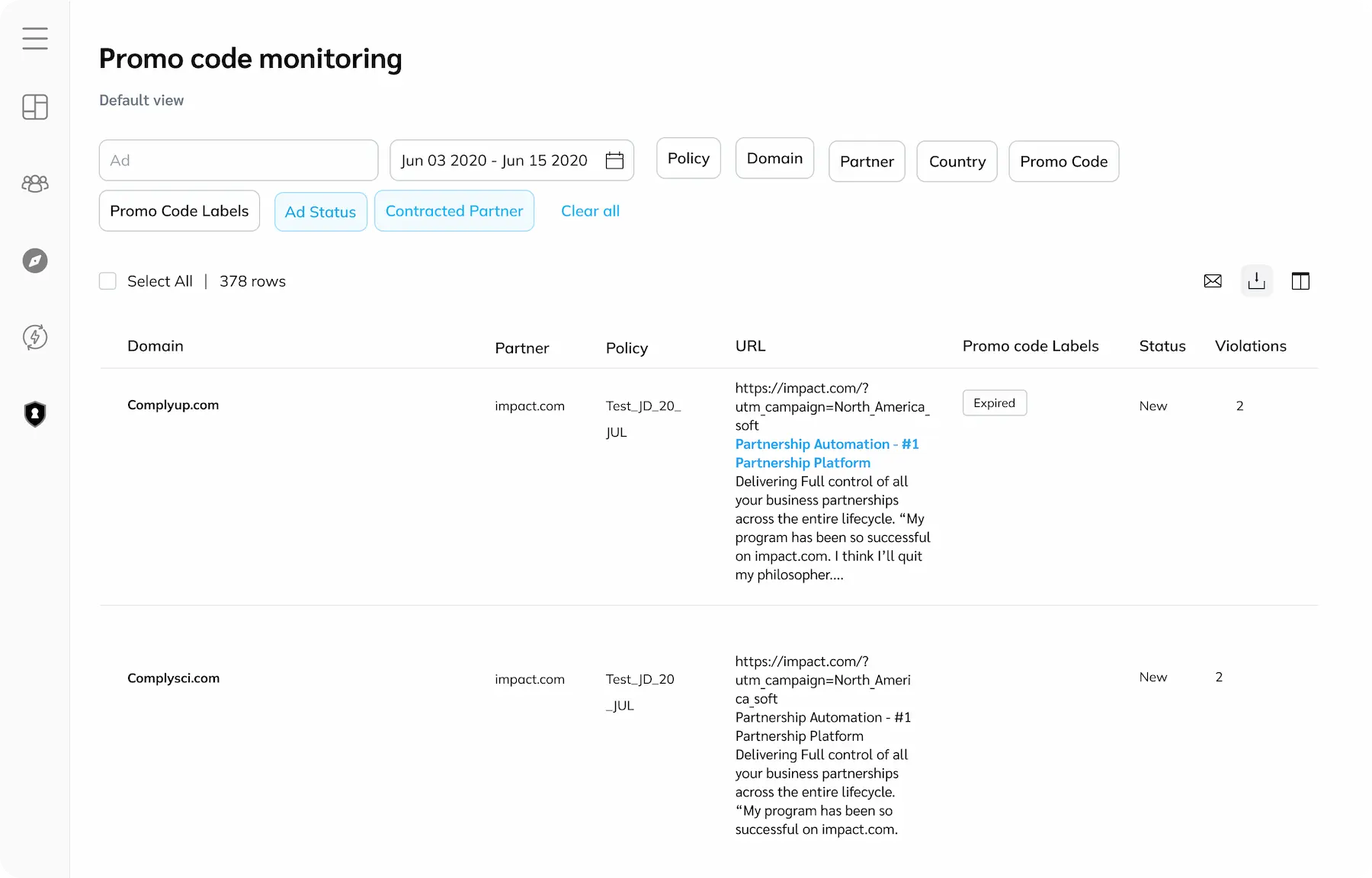
Protect your promo codes from misuse
Promo Code Monitoring helps you maintain a positive customer experience and prevent issues like shopping cart abandonment, reputation damage, and revenue loss. By identifying expired and unauthorized promo codes used by publishers, brands can ensure a seamless shopping experience for their customers.
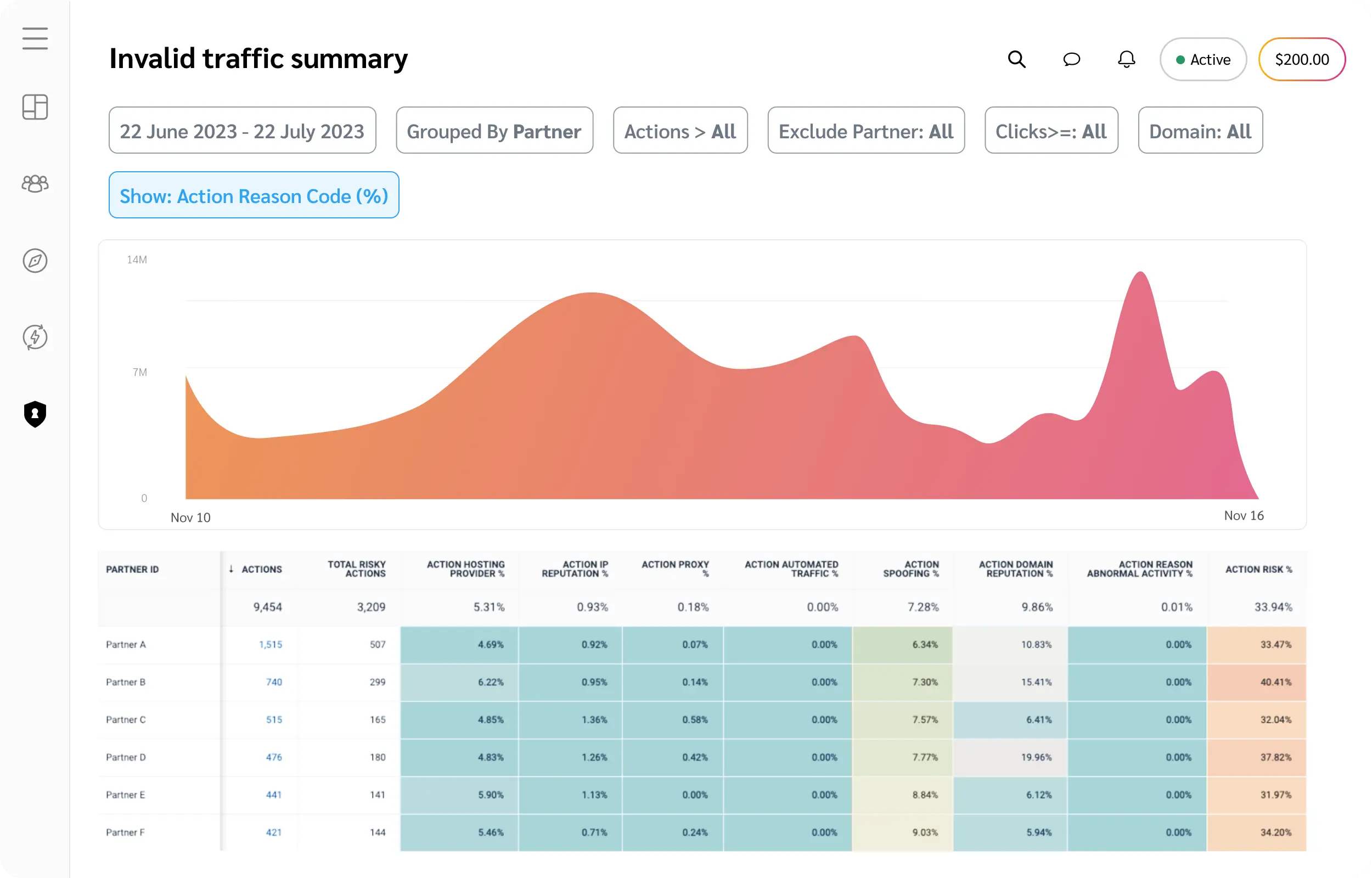
Stop paying out for fake leads or conversion events
Performance fraud poses a threat in both web and mobile environments. With impact.com’s sophisticated Invalid Traffic detection, you gain real-time insights into suspicious traffic sources, with prompt identification of high-risk events, from bot clicks to cookie stuffing. By uncovering the true quality of your partnerships, you can confidently ensure that you only pay for legitimate and actionable outcomes.
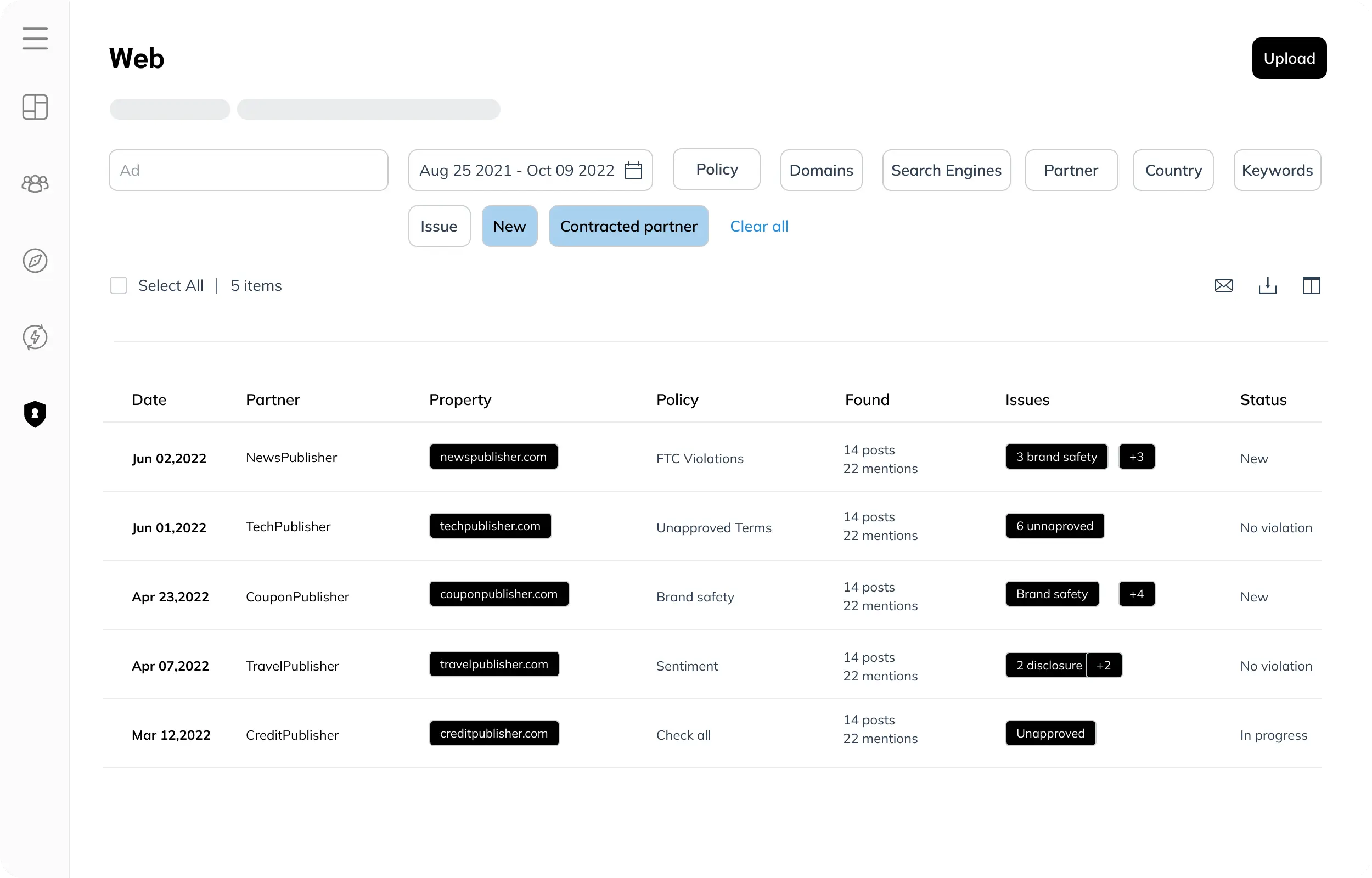
Don’t fear the regulator
Does the thought of hundreds of independent partners promoting offers in your highly regulated industry keep you up at night? Our compliance tool and services let you sleep like a baby.
Prevent liability, ensure accurate content, and avoid nasty surprises with continuous monitoring of your partners’ copy, creative, and offer details. If anything is off, we’ll let you know.
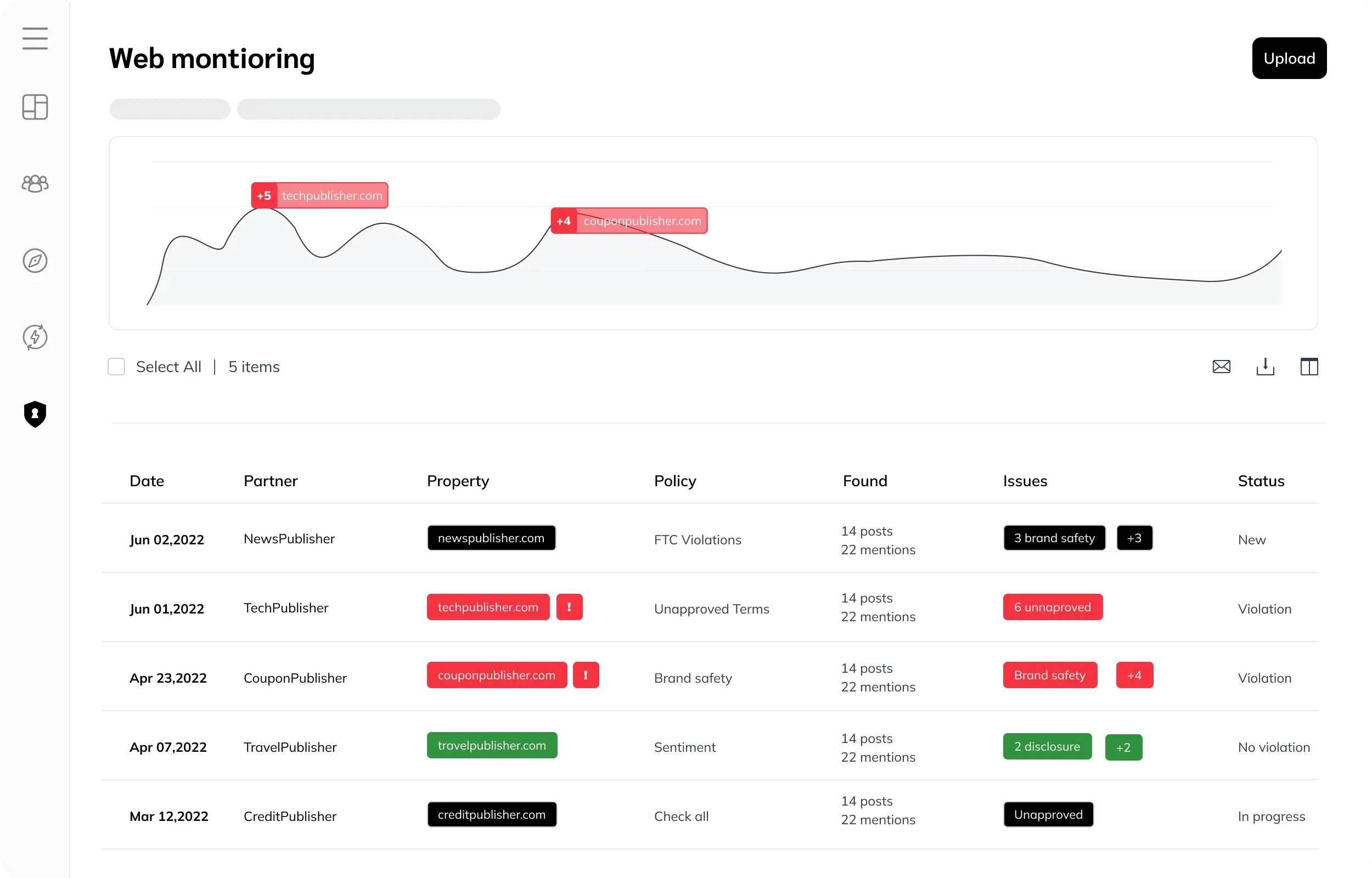
Ensure brand safety
Track the promotion of your brand by your partners with Web Monitoring. Say goodbye to multiple third-party platforms—impact.com offers comprehensive brand safety tools. Regular web scanning uncovers potential risks that could harm your reputation, impede compliance, or undermine customers’ confidence in your product and brand.
impact.com partnership management platform
Manages, protects, and optimizes all of your organization’s different partnerships. Learn more about how we can help you scale faster.
Discover & Recruit
Discover a limitless number of global partners—and add them to your partnership program with ease. Save time with powerful discovery and recruitment automation.
Contract & Pay
Choose your business outcomes, then reward the partners that drive them.
Track
Track the traffic partners drive on all your properties, across any device.
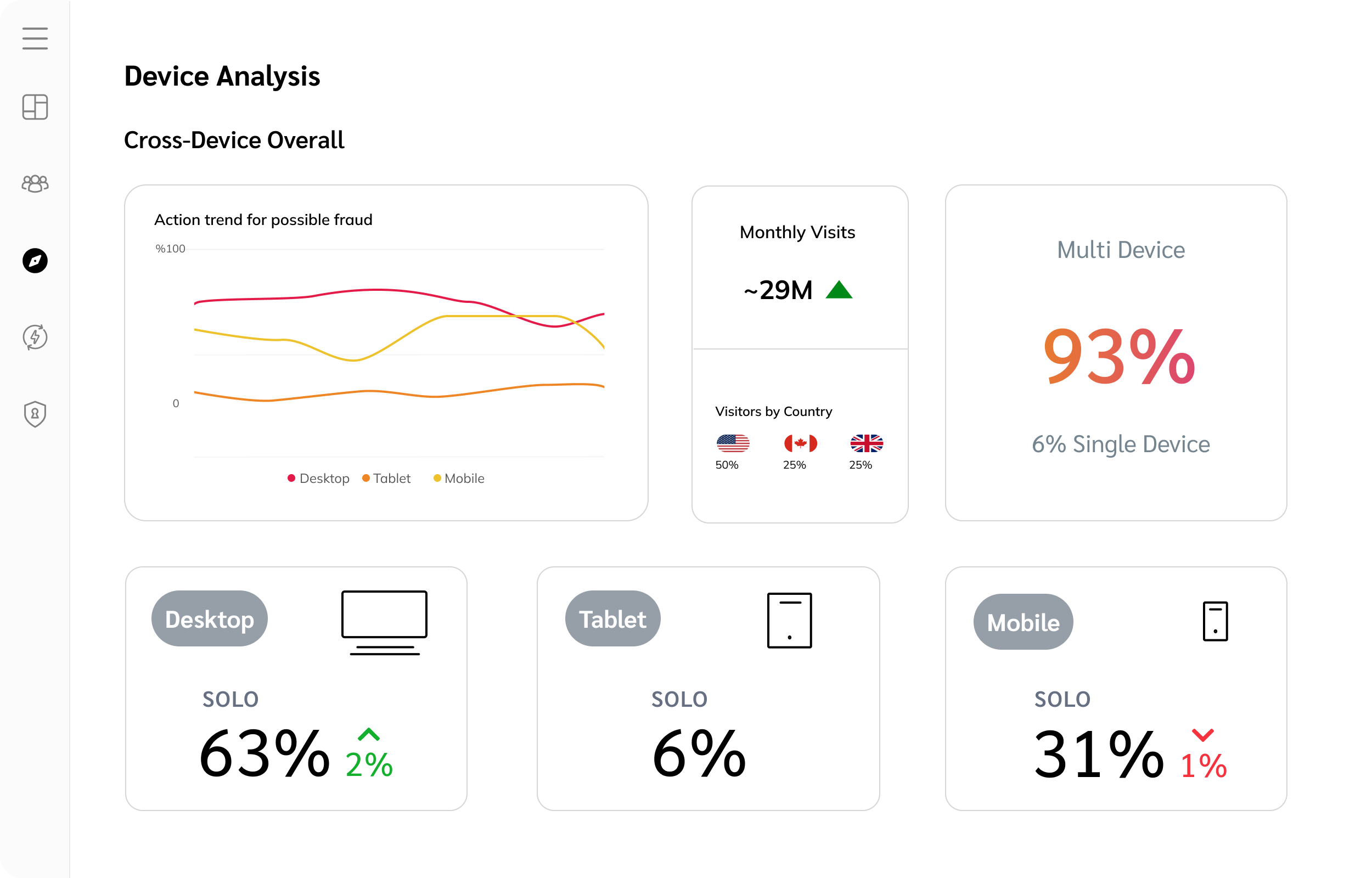
Engage
Proactive messaging and automated workflows make sure partners stay informed, productive, and on-brand.
Protect & Monitor
Fortify your partnerships with full-stack protection across the entire consumer journey. Automate the daily monitoring and remediation of issues that could result in partner non-compliance. Expose affiliate fraud, influencer fraud, and traffic abnormalities wherever they corrupt your conversion paths. Cut out invalid traffic and reinvest spend in high-quality partnerships.
Optimize
Continually optimize your partnerships for growth and efficiency.